Massive cyberattacks slam official sites in Russia, Ukraine
Loading...
The back-and-forth volley of cyberattacks that began last week between Ukraine and Russia hit its highest pitch yet Monday, with Russian websites slammed by an onslaught designed to flood websites until they become unusable.
The open cyber flareup began last Thursday when attacks clearly originating in Russia targeted an unidentified computer network in Ukraine. The next day, a powerful attack temporarily knocked out websites for the Kremlin, the Russian central bank, and Russia’s Foreign Ministry, though Russian authorities said the attack had nothing to do with the Ukraine crisis.
On Sunday, Ukranian government websites were hit by a wave of 42 cyberattacks during Crimea’s vote to secede from Ukraine and join Russia. The type of attacks being observed are all distributed denial of service (DDoS) attacks, which clog websites with bogus data, and they echo the DDoS attacks Russia used in 2008 when it invaded the former Soviet state of Georgia.
But Monday, a day after the vote, brought easily the largest and most powerful attacks, including 132 separate DDoS blasts slamming Russian sites. They included one that was 148 times more powerful than anything Russia did in Georgia in 2008, and four times larger than the attack launched from Russia last Thursday, according to Arbor Networks of Burlington, Mass., which tracks such attacks.
The largest attack against Russian websites Monday registered 124 gigabytes per second of spurious data targeting a single network for about 18 minutes – plenty long enough to overwhelm and take down its target, experts said. The largest attack against Georgia in 2008 hit only 843 megabytes per second.
By contrast, Monday saw just four reported DDoS attacks targeting Ukraine with the peak size 9.8 gigabytes per second.
“There are multiple types of attacks being thrown against some of the targeted sites,” writes Jason Jones, an analyst at Arbor Networks, in an e-mail interview. “From the botnet tracking perspective, it has definitely a back and forth between Russia and Ukraine sites being targeted....”
Targets of the attacks were not identified by Arbor Networks, according to company policy, and many of the attackers could not be identified because the attacks were diffused across so many attacking computers worldwide. But at least some attacks against Ukraine could be tied to two large criminal botnets – millions of computers worldwide that are infected and controlled by malware from cyber criminal gangs. Botnets are often rented out to conduct DDoS attacks.
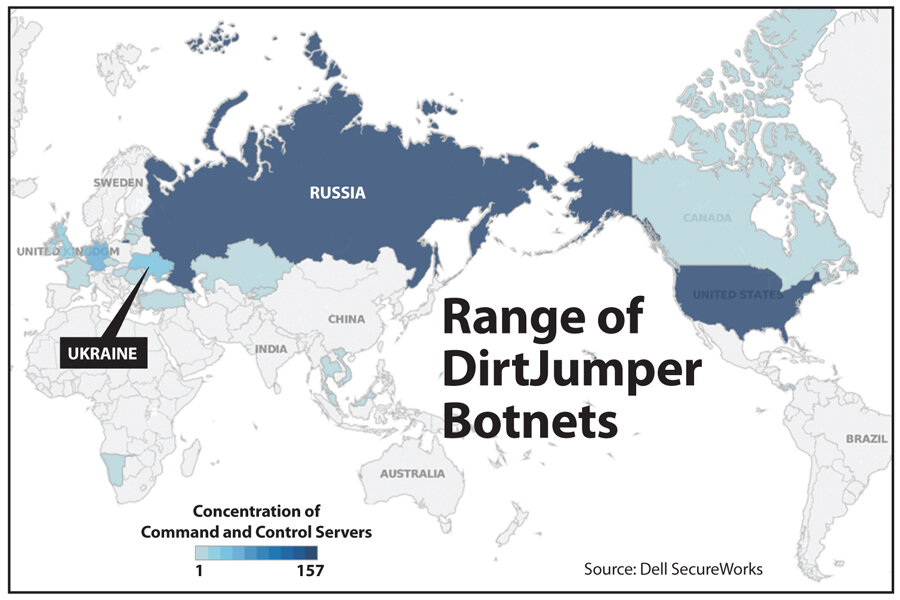
On Friday, Dell SecureWorks Counter Threat Unit (CTU) research team observed a family of Eastern European criminal botnets, dubbed DirtJumper, include on their target lists for DDoS attacks “numerous pro-Ukranian government websites, including Ukranian news media outlets,” writes Elizabeth Clarke, a spokesman for the company in an e-mail. DirtJumper was also active in early December, when CTU saw two DirtJumper botnets being used to DDoS Ukranian government sites.
It’s hard to see any national allegiance linked to the DirtJumper botnet attacks, especially since, in theory, anyone with the cash can rent them. DirtJumper command and control servers exist in Ukraine and Russia and other nations, but with the majority in Russia, Dell SecureWorks reports. Historically they have been used, and continue to be used, by criminal groups to DDoS financial institutions as the criminals make fraudulent wire transfers, Ms. Clarke notes. The goal is to distract the financial institutions' security team.
Botnets controlled by Russian cyber criminals were used in DDoS attacks on Estonia in 2007 and Georgia a year later, several analysts have since reported. But most of the Monday attacks against Russia could not be definitively tied to a particular country, Arbor Networks experts said. In one case, however, Russian media on Sunday fingered the United States.
“US hackers target Crimean referendum website,” the Kremlin-run Voice of Russia reported Sunday, according to National Public Radio. The Russian news service cited vote organizers who claimed the attacks were linked to computers at the University of Illinois at Urbana Champaign, NPR reported.
Meanwhile, a NATO spokesman tweeted that the organization's homepage and other websites were hit by a "significant DDoS attack" Saturday and Sunday. But the NATO main web server was reportedly restored Monday; and others, a few hours later. A hacker group called CyberBerkut claimed responsibility for the attack it said, in a statement, was intended to protest NATO involvement in the Ukrainian crisis.
The heavy cyber fusillades follow what had been a calm period with relatively few overt attacks before last week. One exception was the detection of Russian cyberespionage malware called “Snake” in Ukrainian government systems.