Introduce intelligence to your security operations
Loading...
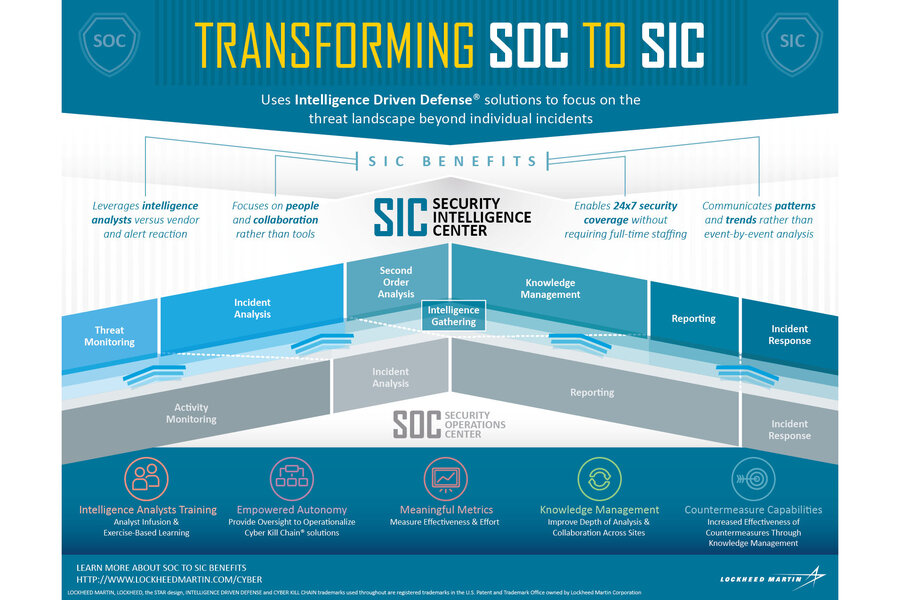
Traditional security operations centers (SOCs) have done well protecting against traditional attacks. The problem is that in today’s threat landscape, characterized by advanced persistent threats (APTs), a traditional SOC misses the mark. We now require a heightened level of security that brings intelligence analysis and knowledge management to the forefront. A security intelligence center (SIC) empowers organizations to address these threats before they cause harm, rather than merely reacting to them. If the data has been taken, a reaction will only do so much.
The cornerstone of a successful SIC is an intelligence driven-defense framework. This presents organizations with a clear strategy for addressing rising threats head-on. Intelligence driven defense emphasizes solutions and tradecraft beyond individual incidents and leverages intelligence analysts rather than relying on vendors and reaction to security alerts. This allows analysts to stay ahead of the adversaries.
The Cyber Kill Chain, key to the intelligence driven defense, is also integral to the success of a SIC. It describes seven phases of intrusions and represents our approach for defeating advanced persistent threats. Although these threats represent a smaller percentage of network intrusions, they are the most difficult to detect and are potentially the most damaging.
There are many advantages to applying the Cyber Kill Chain and moving to intelligence-driven defense, such as:
- Prioritize Sensor Alerts – Focus on warnings further along the Cyber Kill Chain, as those are the most likely events that will lead to the worst breaches.
- Determine Escalation – Not all breaches are equal: Delivery of a malicious email is not as critical as active command and control between an adversary and an infected enterprise machine. This aides in determining which events to to communicate to senior management.
- Measure Effectiveness – An enterprise is more effective when it stops attacks earlier in the chain.
- Determine Resiliency – Are you secure against an attacker against multiple steps of the Cyber Kill Chain, or if a previous attacker changes one aspect of their attack profile will they succeed the next time?
- Maximize Investment – Be sure to compare tools or solutions against each other. If they are both designed to stop at the same stage in the attack, do you view them in this light, or do you just see more tools as enabling “greater security” and fail to make the shrewdest investment decisions?
- Measure Analytic Completeness – After an attack, rather than celebrating the success, play out the rest of the attack to see what would happen next and build resilient systems accordingly.
- Identify and Track Campaigns – Do you understand discrete events and determine when the same adversary and tactics are involved? While this is a higher-order of maturity in network operations, it is attainable when a team properly leverages the Cyber Kill Chain and intelligence-driven defense.
The good news is a SIC gives the defenders the ability to win. Despite countless attempts on strategically valuable assets (as encountered by Lockheed Martin every day), using intelligence analysis gives defenders the upper hand. But that advantage does not just come from using the best tools — it comes from skilled analysts who know how to employ those best tools and information that can be gleaned from intelligently defending the enterprise.
Greg Boison is the Director of Lockheed Martin’s Homeland & Cybersecurity line of business. This diverse portfolio includes capabilities in systems integration, software development, enterprise IT, credentialing, biometrics, and cybersecurity. Follow Greg on Twitter @gregboison.