Centcom Twitter hack and the rewards of digital vandalism
Loading...
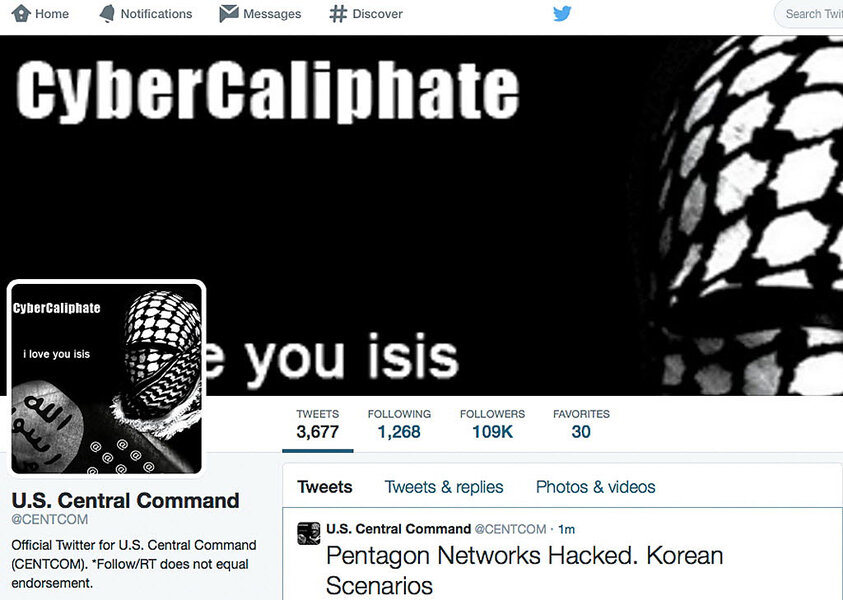
When US Central Command’s social media sites were taken over by the "Cyber Caliphate" earlier this week, it marked the third time in recent days in which unknown hackers defaced websites with messages supporting the Islamic State, the jihadi group fighting in Iraq and Syria.
Vandalism of Twitter and YouTube accounts or a TV station website is hardly a challenging cybercrime. Yet this recent rash of digital graffiti, even if it's the work of pranksters, has handed the militants a public relations victory in a fight against the West taking place on battlefields and online.
"It makes the US military look silly," says Ben Fitzgerald, director of the Technology and National Security Program at the Center for New American Security in Washington. "The Cyber Caliphate looks more technologically savvy than Centcom, which isn't the case."
Before unknown hackers took over the Twitter and YouTube accounts belonging to Central Command, or Centcom, similar attacks last week hit the website of WBOC-TV, a local TV station in Salisbury, Md., and a New Mexico daily newspaper. In all three incidents, the attackers posted messages in support of the Islamic State.
While hitting sites and social accounts for small media outfits might not give the Islamic militants or their supporters much credibility, defacing Centcom is a different story. After all, this is the military command post from which the US oversees operations in the Middle East, where American forces have been battling IS militants.
"At the same time it has suffered a series of setbacks on the physical battlefields of Iraq, the ISIS flag got waved in a medium that more people in the West both notice and care about – the social media environment," Peter Singer, a strategist for the New America Foundation, wrote in Wired. "It further stakes ISIS’s claim to prominence among the next generation of jihadis."
Indeed, social media has become an important tool for recruiting fighters to militant movements. In a Monitor article last year, Matthew Olsen, director of the National Counterterrorism Center, was quoted as saying: "Importantly, the group also views itself as the now-leader of a global jihadist movement ... and it uses social media to secure a widespread following."
Still, it's difficult to know who was really behind the recent spate of IS related cybervandalism, and most experts doubt it's anyone directly tied to the militant group.
"It’s very difficult to establish attribution in these cases," said Fitzgerald. "But the most interesting thing I saw on Twitter was a screen grab of who the Cyber Caliphate was following. One of the accounts it followed belonged to Andrew Jackson Jihad, a folk punk band based out of Phoenix, Arizona. There wouldn’t be a lot of fans of a band like that in Syria or Iraq."
But whoever it is, said Stuart Baker, former assistant secretary for policy at the Department of Homeland Security, "It suggests that security wasn't a high enough priority across the command."
Now, said Mr. Baker, that's likely to change. "We should see less of these attacks because people should be more aware," he said. "Both Twitter and Google have offered two-party authentication tools that can be used to prevent this."
The FBI is investigating all three attacks.